SysAdmin Weekly #1
The debut edition of SysAdmin Weekly - Podcast links, tools, CVEs, community posts, and not a single reboot required.
🖥️ SysAdmin Weekly - The Newsletter
May 27, 2025
Welcome to your weekly dose of IT sanity, served piping hot. Get that coffee ready!
Let’s get into it!
🎙️ The Latest on the SysAdmin Weekly Podcast
🎧 Inside Microsoft Certifications in 2025
This week Andy Syrewicze and Paul Schnackenburg talk all things Microsoft Certification. This includes current certification paths, embedded training during certification exams, how MCTs are shaping the next wave of sysadmin upskilling, and LOTs more. Plus, there may or may not be a hot take on how many certs is too many certs.
🔍 From AndyOnTech and Project Runspace
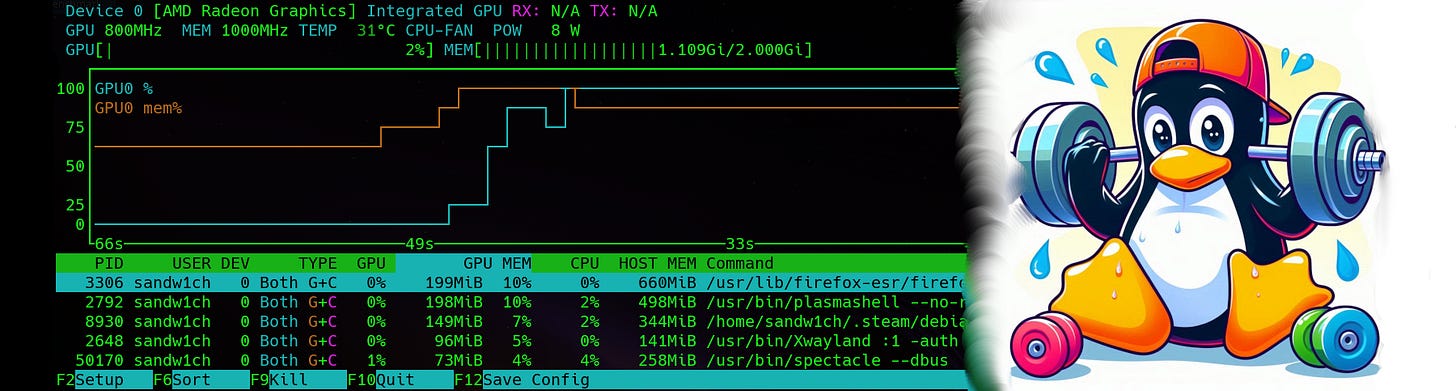
🧪 How to Stress Test a Linux Box Like a Boss
A practical guide to pushing your Linux servers to the edge so you can make sure you’re getting EVERY ounce of performance you (or your company) paid for. This post will show you how to stress test CPU, RAM, disk I/O, GPU, and networking!
🖥️ How to Install Windows Server 2025
A step-by-step guide for getting Server 2025 up and running in your lab or prod environment. Windows Server 2025 is new, and there are JUST enough changes previous versions that it’s worth having a look prior to your first installation.
🧵 Helpful Community Blog Posts
🔐 Register YubiKeys On Behalf of Users
Tired of support tickets from users who won’t enroll their MFA tokens? Jan Bakker to the rescue with YubiEnroll which is a tool that makes it easier for SysAdmins and help desk staff to enroll YubiKeys on behalf of users.
☁️ Designing A Hub And Spoke Infrastructure
Aidan Finn walks through the planning and principles of building a hub-and-spoke network in Azure. If you’re looking to follow the best practices and get guidance from an expert in Azure virtual network architecture, start here!
🧼 PowerShell Script to Clean Up Your Az Modules
Too many Az.* modules cluttering up your PowerShell profile? This script from Didier Van Hoye makes it painless to purge old cruft. I was looking for something JUST like this the other day, so it warrented a mention!
🛠️ Tool of the Week
GoBuster – Because even your directories have secrets.
GoBuster is a fast and flexible brute-forcing tool used for directory and file discovery, DNS enumeration, and more. While it’s often wielded by red teamers and pen testers, savvy sysadmins can flip the script—using GoBuster to probe their own web infrastructure for exposed endpoints before attackers do. Knowing your attack surface allows you to secure your attack surface.
🔐 Security Headlines for SysAdmins
🛡️ Abusing dMSA for Privilege Escalation in Active Directory
Akamai researchers detail how attackers can exploit delegated Managed Service Accounts (dMSA) to elevate privileges in Active Directory. TL;DR: It’s nasty and trivial to exploit. It does assume that the attack has SOME access into the environment already, but there are plenty of ways a threat actor could make those inroads.
📡 SK Telecom Malware Breach Leaks 26M IMSI Records
A new malware campaign hit SK Telecom, leaking sensitive subscriber metadata. Mobile infrastructure defenders, take note this one’s ugly, and also worth a mention because Andy and Paul discussed it briefly on a recent episode of the podcast.
🚨 CVE Alert
Four major vulnerabilities are being actively exploited in the wild.
CVE-2025-32706 – Windows CLFS Driver Privilege Escalation (CVSS 7.8) - Improper input validation in the Windows Common Log File System (CLFS) driver allows an authorized attacker to elevate privileges locally.
CVE-2025-32701 – Windows CLFS Driver Use-After-Free (CVSS 7.8) - A use-after-free vulnerability in the CLFS driver permits local attackers to escalate privileges.
CVE-2025-30397 – Windows Scripting Engine Type Confusion (CVSS 7.5) - A type confusion vulnerability in the Microsoft Scripting Engine allows remote attackers to execute code if a user clicks a malicious link.
CVE-2025-30400 – Windows DWM Core Library Use-After-Free (CVSS 7.8) - A use-after-free vulnerability in the Desktop Window Manager (DWM) core library allows attackers to elevate privileges.S
🛡️ TL;DR: If you’re running Windows systems, patch these vulnerabilities immediately to mitigate active threats.
☕ Wrap Up
Fun Fact:
The first computer virus for IBM PCs was called Brain, created in 1986 by two Pakistani brothers.
Originally designed to deter piracy of their medical software, it ironically became one of the most widespread early PC viruses. It even included their names, address, and a phone number for “tech support” (or possibly moral scolding).
Read more: Brain (computer virus) – Wikipedia
See you next week!